A vast amount of electronic evidence is being transmitted everyday via electronic file transfers among corporations, law firms and e-Discovery service providers. Most of these transfers involve compressing the evidence into a file containers (ZIP, RAR, 7z etc.) and transferring the resultant archive(s) over the internet. While this is usually a straightforward process, it is critical to make the right decisions and use the right tools to avoid trouble down the road.
Preservation of Metadata in File Containers
One of the most common issues associated with compressing electronic evidence into file containers has to do with the preservation of metadata. Unless proper care is taken, compressing electronic files can result in loss of valuable file system metadata.
In our experience, the most common file compression tools used in e-Discovery are WinZip, WinRAR and 7-Zip. Surprisingly, some of these applications do not capture and restore file system timestamps by default. The following table summarizes which metadata timestamps can be preserved using each software:
| WinRAR 4.11 | WinZip 15.5 | 7-Zip 9.20 | |
|---|---|---|---|
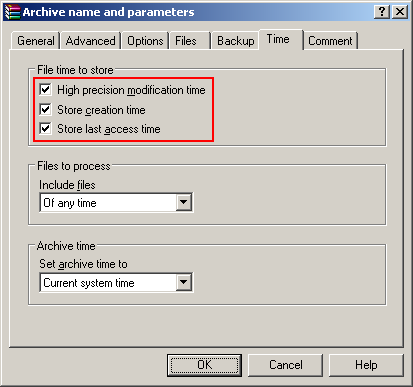
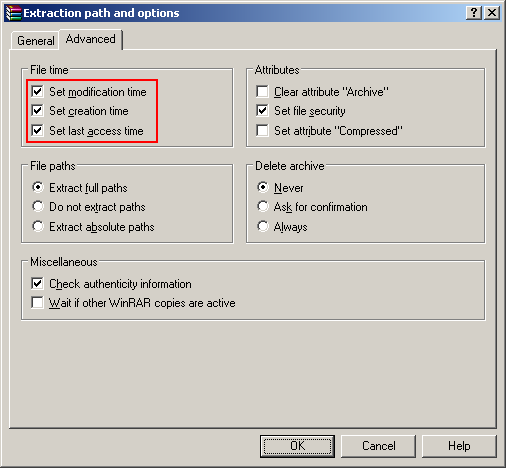
| Creation Date | Default: No Yes (Optional) |
Always | Never |
| Last Modification Date | Always | Always | Always |
| Last Accessed Date | Default: No Yes (Optional)* |
Always* | Never |
| * When the option is available, the stored last accessed date is the date/time when the files were accessed while creating the file container. When not available, the last accessed date is set to the date/time the files were extracted. | |||
Table 1 – Date Metadata Preserved by File Archive Software
Based on the table above, only WinZip and WinRAR support preserving file creation dates. WinRAR captures file creation timestamps only after the option is selected while WinZip captures them by default. Consequently, if files were compressed using 7-Zip, or using WinRAR without the correct date options, their file system creation timestamps would be stripped off. This means that even if the electronic evidence was collected properly and file system metadata was preserved, the compression process can prevent this information from being transmitted to the recipient.
The relevant options during compression and extraction in WinRAR are as follows:
Encryption
Security is always a valid concern when evidence is transmitted electronically. When compressing files into file containers, we recommend using encrypted archives as an additional security measure. The encryption password should be strong, and different than the credentials required to access the file transfer system. WinZip and 7-Zip support AES-256 encryption while WinRAR uses a maximum AES key size of 128 bits. WinRAR and 7-Zip support encrypting file names while WinZip does not.
Long File Paths
Another common issue is compressing or decompressing files with very long paths. In most cases, you can work around this issue by mapping the source (if compressing) or destination (if decompressing) folder path as a network drive and accessing the files through that drive letter. For example, let’s assume that the files we would like to compress are in the following folder:
\\server\share\Case Documents\Client Name\Sources\Case Name\Date\Data Set 1
We can map this folder to a drive letter such as Z: using the following command:
We can now compress the contents of, or extract the files to the Z: drive. In this example, this would shave 73 characters off the file paths.
Conclusion
- It is important to choose the right file compression tool and familiarize yourself with all available options. We typically recommend WinRAR as it provides a combination of good performance, compression and security features when working with file containers.
- Encrypting file containers before sending them over the internet can be a valuable additional security measure.
- In most cases, file paths that are too long can be accessed by mapping the parent folder as a network drive.